Why are McDonald’s Self Service Kiosks so hackable?

McDonalds in Australia do a decent cup of coffee. It’s not great but it’s consistently decent so I often start my day with a cup. Due to my travels around Australia in a decked out van I have seen how many McDonalds operate and just how many of these terminals are left fucking unlocked.
Underpaid staff who used to do ordering have been replaced with these self-service kiosks and a process that is based off to tickets. This process completely falls apart when the ticket printer runs out of paper and as McDonalds does A LOT of orders the printers run out of paper often. From what I've observed staff across Australia are leaving the Kiosks unlocked to make it easier to replace the paper.
Inside a kiosk is a standard x86 computer NUC with exposed USB ports. Now I’ve learned since my youth but part being a hackerman is having keen observations for really dumb stuff that can be leveraged and you never lose that skill even after you cease practicing. It’s like travelling to a new town with a skater boi - always looking for new lines to skate.
Three days ago at the Blaxland store my spider senses started tingling when I noticed something quite alarming. It turns out that these kiosks run windows as administrator, touch screen input is enabled and in the recovery operating mode the general public can run any application 😬
CVE-2022-244622: A local unauthenticated attacker within a @McDonalds could exploit this knowledge to pop calc.exe.
— GEOFF 🦩🎼🌷 (@GeoffreyHuntley) July 22, 2022
The default user on the terminals is Administrator and touch screen input is enabled. pic.twitter.com/uG1pXG6iYb
So why am I concerned? Why should you care? There are payment terminals attached to these kiosks. If someone installs malware on here - just insert a usb stick or use the recovery mode - then tada we have the next generation of atm skimming.

Today at another McDonald's I observed the entire bootstrap process and can confirm that the kiosk indeed is responsible for installing “custom firmware” on the card reader and as user interaction is enabled, it is, in theory, possible to force the terminals into recovery mode when they boot by tapping on the screen...

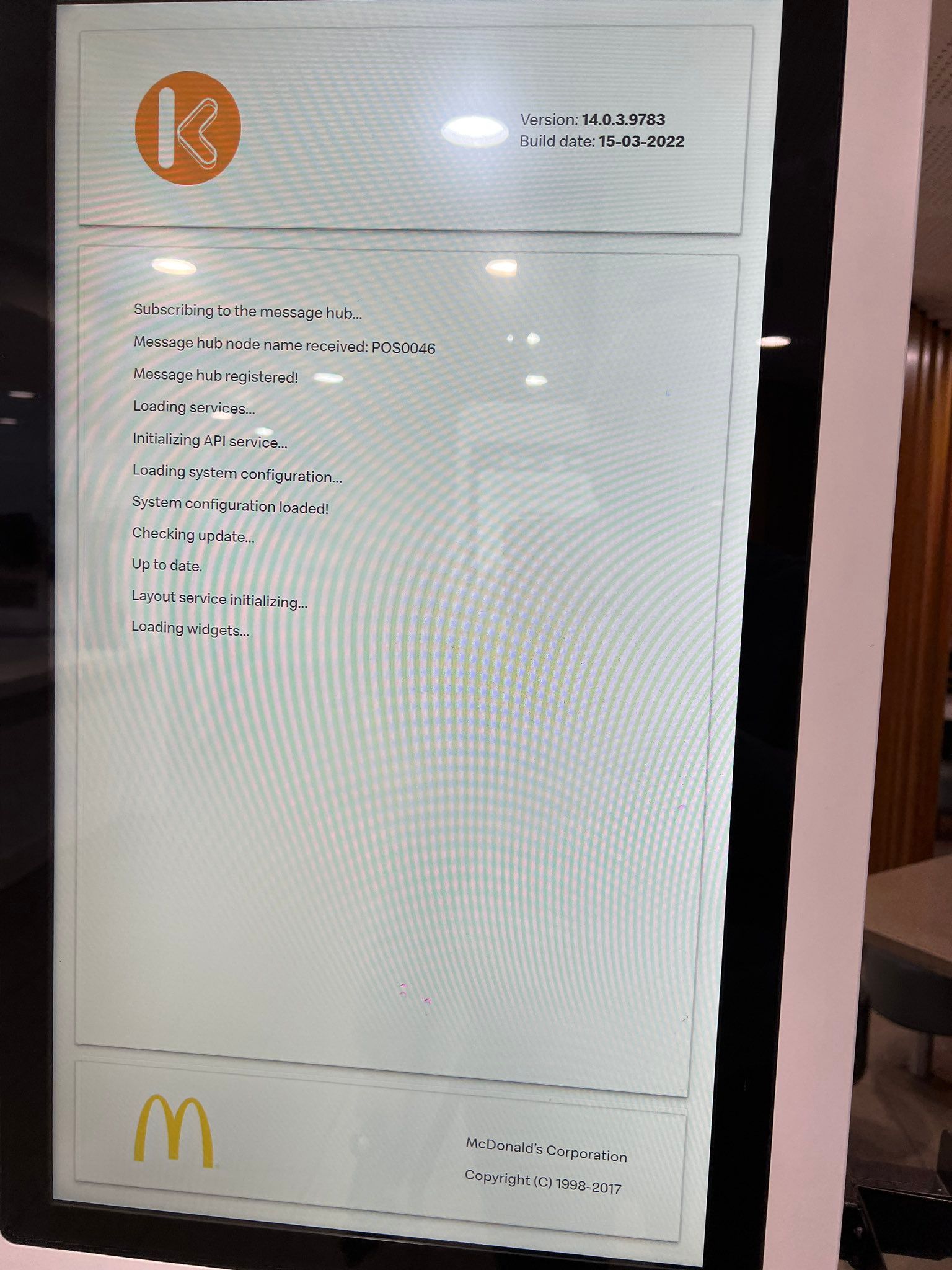
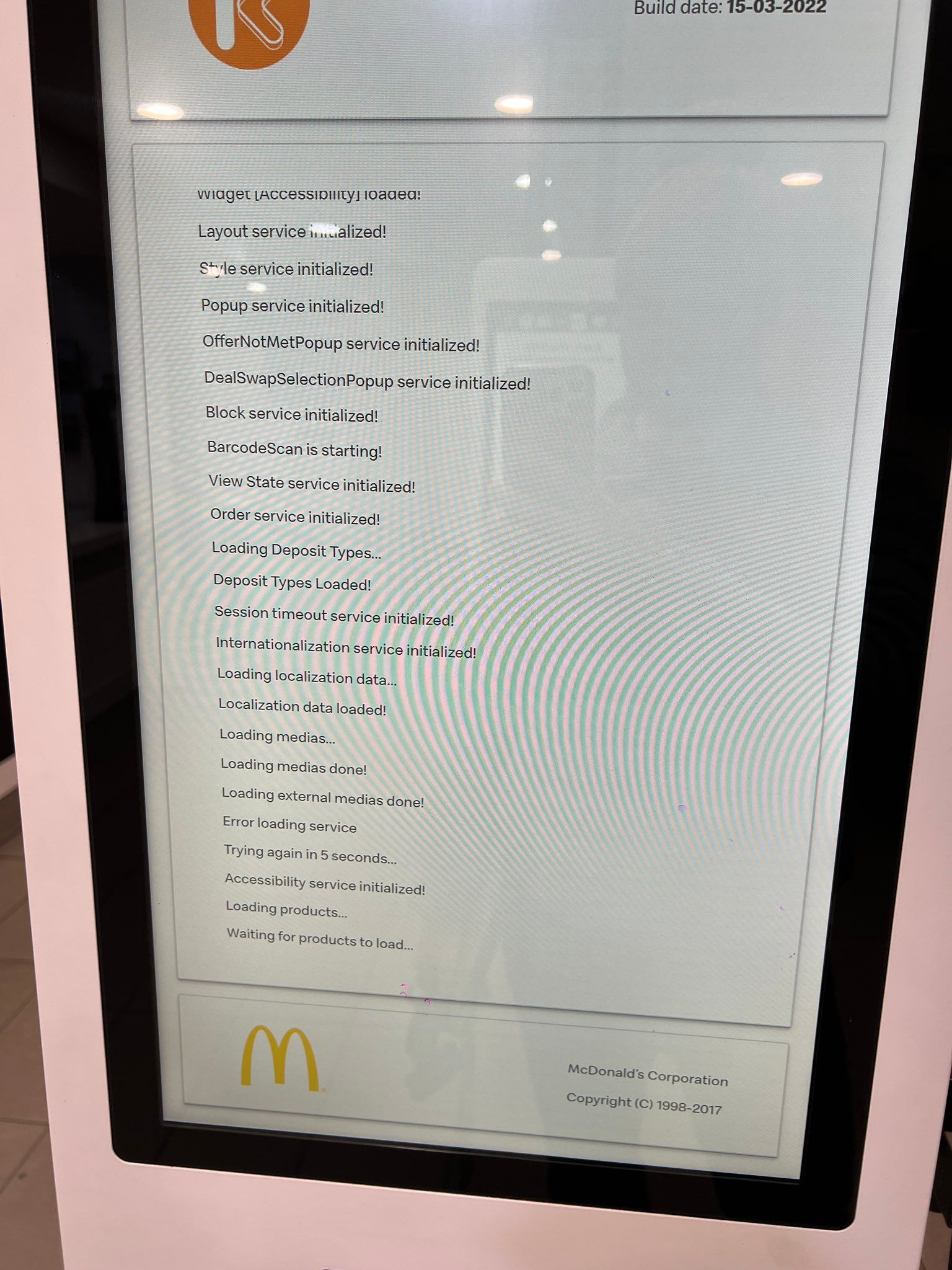

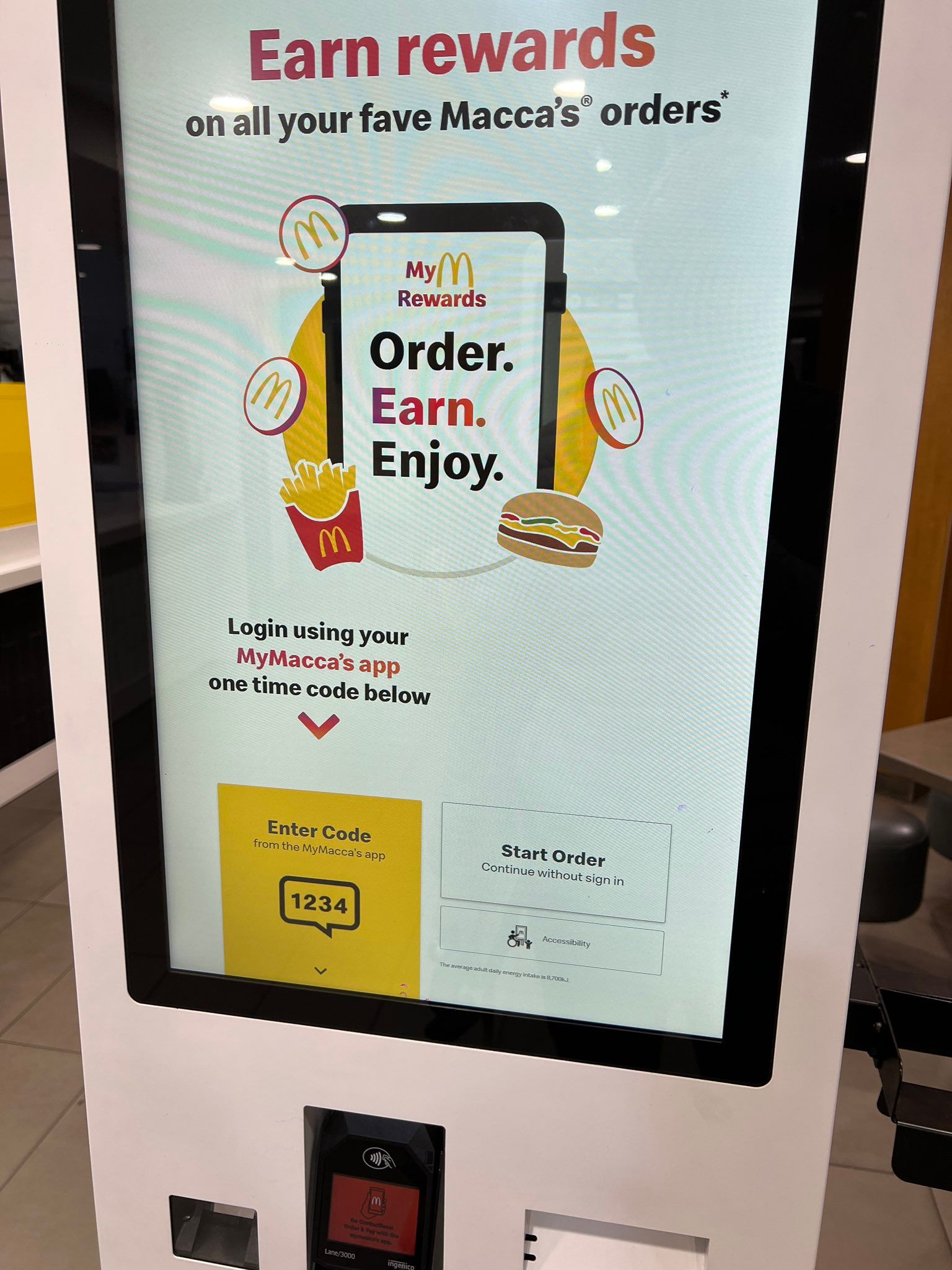
McDonalds your processes are faulty in the following ways:
- The kiosks are built with the design of “they are physically secure so it’s okay to run as administrator”. This is NOT okay.
- The kiosk user interface has error modals which block visibility of what someone’s order number is which creates customer confusion and process dysfunction with people picking up orders that aren’t theirs cause they don’t know what their order number is. Which results in underpaid staff leaving the machines unlocked so that doing a task that they do often can be done easier.

Anyway, so here I am sitting here with my cup of so-so coffee and pondering that it is inevitable that these terminals will be used for financial crime in the future whilst opsec (store employees and kiosk machines running as administrator) remains so relaxed.
Knowing all of above I no longer use these Kiosks and recommend you don't either.
What someone does with this knowledge is left as an exercise to the reader but it would be delightful to see b-sides talk where someone who has legally obtained one of these terminals up on stage just as Barnaby Jack did with ATM's in 2013 at DEFCON.
ps. If you made it this far then maybe you would also enjoy the following...
.@maccas does a decent cup of coffee. It’s not great but it’s consistently decent so I often start my day with a cup. Due to my travels around Australia in my van, I have seen how many operate and how many of these terminals are left fucking unlocked.https://t.co/3QlX9SGd2E
— GEOFF 🦩🎼🌷 (@GeoffreyHuntley) July 24, 2022





